Key Terms Defined
Homeland Security Presidential Directive (HSPD) – 12
On August 27, 2004, President Bush signed Homeland Security Presidential Directive 12 (HSPD-12), Policy for a Common Identification Standard for Federal Employees and Contractors. HSPD-12 directs the implementation of a new standardized badging process, which is designed to enhance security, reduce identity fraud, and protect personal privacy by establishing a mandatory, Government-wide standard for secure and reliable forms of identification issued by the Federal Government to its employees, contractors, and “other” class of individuals.
Learn MoreFederal Identity Credential Access Management (FICAM)
FICAM is the federal government’s implementation of Identity, Credential, and Access Management (ICAM). ICAM is the set of tools, policies, and systems that an agency uses to enable the right individual to access the right resource, at the right time, for the right reason in support of federal business objectives.
Learn MoreFederal Information Processing Standard (FIPS) Publication 201-3 (FIPS 201-3)
This document establishes a standard for a Personal Identity Verification (PIV) system that meets the control and security objectives of Homeland Security Presidential Directive-12. It is based on secure and reliable forms of identity credentials issued by the Federal Government to its employees and contractors. These credentials are used by mechanisms that authenticate individuals who require access to federally controlled facilities, information systems, and applications. This Standard addresses requirements for initial identity proofing, infrastructure to support interoperability of identity credentials, and accreditation of organizations and processes issuing PIV credentials.
Learn MoreSpecial Publication (SP) 800-116 Rev. 1
This publication provides a technical guideline to use Personal Identity Verification (PIV) Cards in facility access; enabling federal agencies to operate as government-wide interoperable enterprises. These guidelines cover the risk-based strategy to select appropriate PIV authentication mechanisms as expressed within Federal Information Processing Standard (FIPS) 201.
Learn MoreArtificial Intelligence/Machine Learning (AI/ML)
Artificial intelligence (AI) is a computer-based approach to activities that normally require intelligence (translating data and information into knowledge) to perform effectively. Machine Learning is a form of artificial intelligence in which computer algorithms learn from data to form predictive models.
Data Visualization
Data visualization is the graphical representation of information and data. By using visual elements like charts, graphs, and maps, data visualization tools provide an accessible way to see and understand trends, outliers, and patterns in data. In short, turning data into information and information into actionable intelligence.
Physical Access Control System (PACS) FICAM Architecture
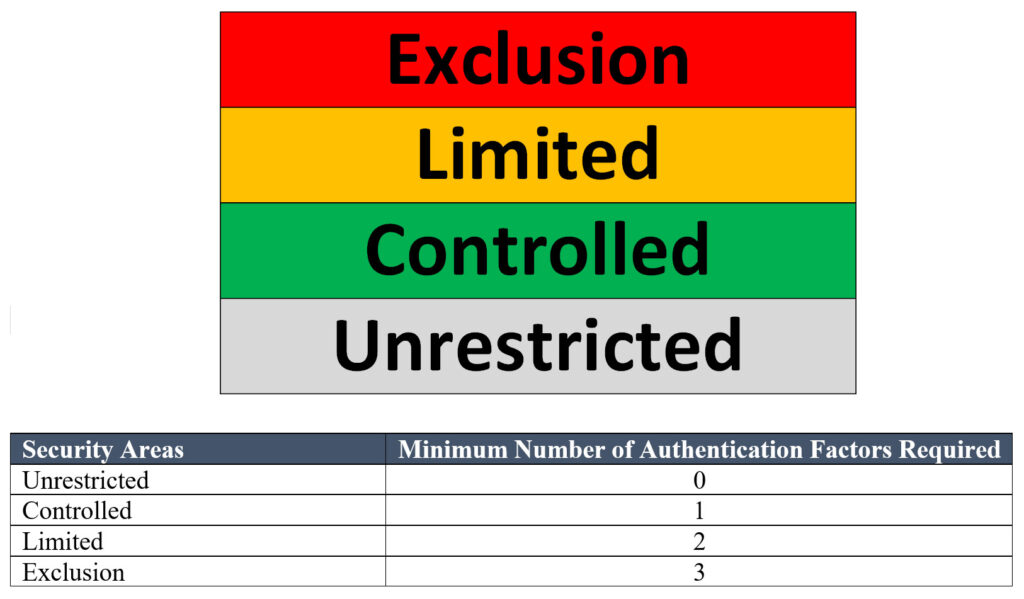
Physical Access Control System (PACS) in Federal Facilities consist of unrestricted, controlled, limited and exclusive areas. One of the functions of the PACS application is to verify the identity of the cardholder presenting a PIV Card or CAC. The PACS application may perform one or more authentication mechanisms using the PIV Card or CAC to establish confidence in the identity of the cardholder. The authentication of an identity is based on the verification of one, two, or three factors: a) “something you have,” for example, possession of the PIV Card/CAC; b) “something you know,” for example, knowledge of the PIN; and c) “something you are,” for example, presentation of live fingerprints or irises by a cardholder.
In Federal Facilities, there are generally four areas of access, Unrestricted, Controlled, Limited and Exclusion and each access areas require varying degrees of authentication. Accessing Unrestricted Areas requires no authentication. Accessing a Controlled Area requires a valid FICAM Credential with a valid Card Authentication Certificate Credential (PKI-CAK) and authorization to access the portal based on date and time. Accessing a Limited Area requires a valid FICAM Credential with, valid known Personal Identification Number (PIN), valid PKI-AUTH certificate and authorization to access the portal based on date and time. Accessing an Exclusion Area requires a valid FICAM Credential with a valid known Personal Identification Number (PIN), valid PKI-CAK or PIV Authentication Certificate Credential (PKI-AUTH), biometric feature (i.e. fingerprint, iris) normally fingerprint and authorization to access the portal based on date and time.